Submarine cables through which electricity and telecommunication networks pass break, leaving cities without communication or electricity. The computer systems of several hospitals in one of the world's largest cities crash, leading to the cancellation of 800 surgical operations. Local governments of a G-7 country lose their internet connection due to attacks on the terrestrial fiber optic network. A series of fires set in fiber optic connections paralyze high-speed trains in two countries.
It's not an apocalyptic tale. All of this has happened in six countries in Europe - Finland, Estonia, United Kingdom, Belgium, Germany, and France - in recent times.
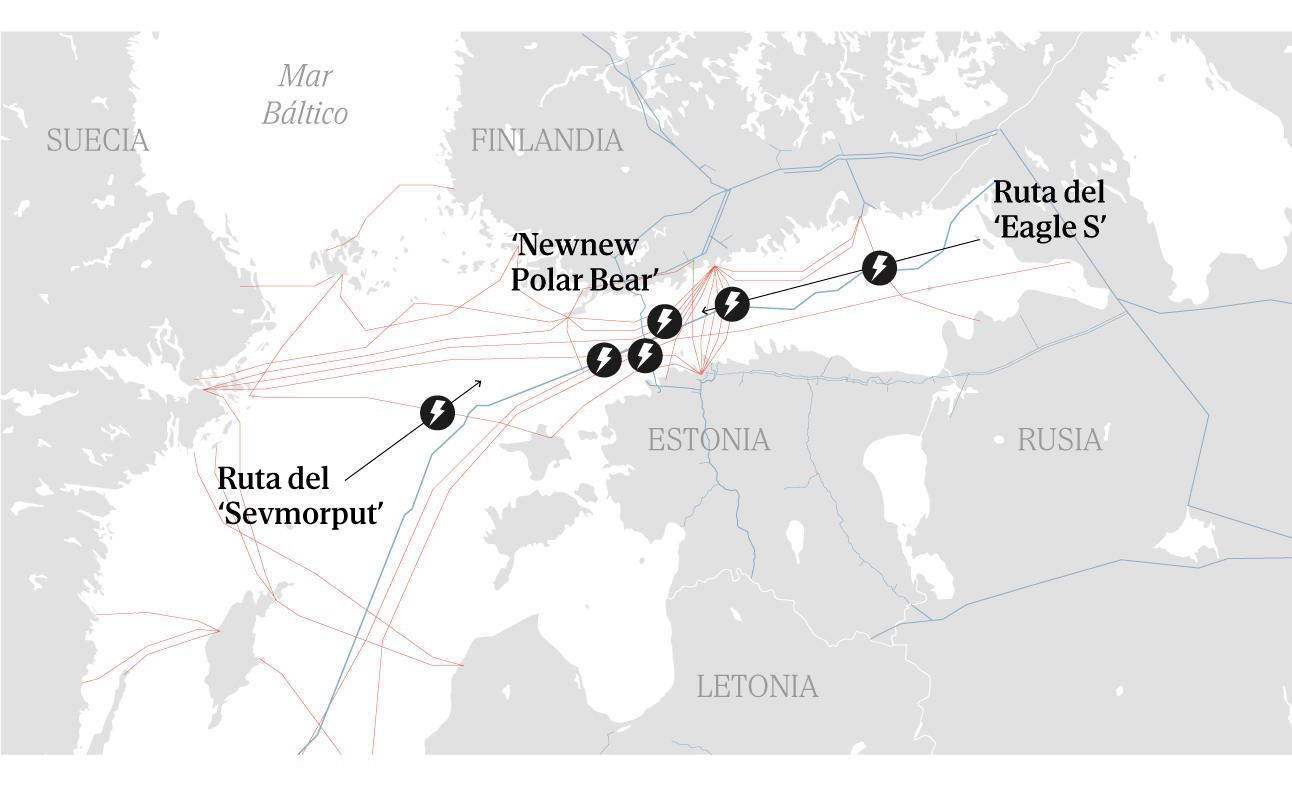
These have been attacks of various kinds. Russian and Chinese ships have broken 11 telecommunication and energy transport cables in the Baltic Sea in the last 15 months. Three major hospitals in London suffered a cyberattack in June. France's fiber optic networks have been sabotaged at least twice - in April and July 2024 - while a series of fires paralyzed almost all of the high-speed train network in that country last summer in an action that also affected passenger rail transport in Belgium, the United Kingdom, and Germany, leaving a million people stranded.
With all these precedents, it is not surprising that the recent closure of London's Heathrow airport - the largest in Europe and the fifth in the world in terms of passenger traffic - due to a fire at a simple electrical substation sparked speculation. The British government's opening of an investigation for possible terrorism reinforced the theory of sabotage, although there is no evidence of it. For now, what the closure of Heathrow has highlighted is the lack of coordination among authorities, with the head of National Grid, John Pettigrew, claiming that there were other available sources of supply at the airport, indirectly blaming the facility's top official, Thomas Wildbye.
These actions only highlight the vulnerability of so-called critical infrastructures worldwide and especially in Europe, a continent that is very technologically advanced, with great integration among different economies, but that had not taken security too seriously until now.
This is where an important player comes into play: Russia. Tensions between Moscow and the West, the invasion of Ukraine, and now the cold war between the European Union and Russia could end up making European critical infrastructures the battlefield. As stated in November by the former director of the Federal Office for the Protection of the Constitution - which is Germany's intelligence service - Thomas Haldenwang, "we have been observing aggressive actions by Russian intelligence services for some time. Russia is using all tools, from influencing political debates to cyberattacks on critical infrastructures or significant sabotage actions."
But even if a détente were to be achieved between the EU and the UK with Russia, it is likely that the latter would continue this asymmetric warfare against infrastructures. "When Russia looks at the West, it does so from a perception of relative weakness. This leads them to adopt a strategy of overreaction and excessive aggression," explains a person who has held official positions in that country. According to this theory, "whether the war in Ukraine ends or not, the Russians will use the cyber domain to attack. Their goal is to demonstrate that, if they want, they can cause a lot of harm." This is the realm of hybrid warfare, a concept coined 18 years ago that combines different forms of combat - from propaganda to direct actions, including sabotage and cyber warfare - and to which the GRU, the Russian Armed Forces' intelligence service, devotes a significant part of its efforts.
The fear of these Moscow actions is precisely one of the reasons behind the tensions between the EU and Russia. In Europe, many believe that Russian President Vladimir Putin uses attacks on critical infrastructures as a way to test the political will of the West. For proponents of this theory, if Russia achieves a peace agreement in Ukraine that it considers favorable to its interests, it will prepare to attack the Baltic countries in the future. Meanwhile, Moscow will test European political will and technological capabilities through cyber warfare and sabotage actions against these infrastructures.
For Russia, "attacking critical infrastructures is the gold standard," explains Alejandro Romero, founder and CEO of the digital intelligence company Alto Intelligence. A report from the American think tank Center for Strategic and International Studies (CSIS) published on the 18th of this month states that critical infrastructures, understood as oil and gas pipelines, the power grid, and submarine cables, have accounted for 21% of Russia's actions against the West in the last three years. But if attacks on transportation networks and companies - concepts that many consider part of critical infrastructures - are added to that figure, the percentage reaches 69%. According to the report, Russia carried out three attacks against Europe in 2022; in 2024, the number had already reached 34.
The actual numbers are likely higher. "There are many hybrid threats that go undetected or, if discovered, there is no evidence to attribute responsibility to anyone. This is the case in Europe, where Russia has been attacking critical infrastructures below the detection level for 20 years," says Romero, adding that "the attacks also serve to gather information, intelligence, and test the adversary's resilience."
The fragility of critical infrastructures is partly a consequence of economic growth itself. According to the specialized consultancy IoT Analytics, by the end of last year, there were 18.8 billion devices connected to the internet worldwide. This generates an endless list of risks for infrastructures. This is how the term critical infrastructures, popularized 29 years ago when Bill Clinton created an advisory commission to improve their management and security, has expanded today to encompass almost all economic activity. Currently, critical infrastructures cover 11 sectors, ranging from food and distribution to the cloud. As explained by Nicolás de Pedro, a researcher at the British think tank Institute for Statecraft, "we are discovering that there are many more critical infrastructures than we thought, and attacking them is very cheap."
Some of these vulnerabilities are extremely sophisticated. Last year, the US decided to subsidize the manufacture by the Japanese company Mitsui of port cranes for container ships. The goal is to replace the cranes from the Chinese state-owned company ZPMC, which, according to Washington, have software that identifies the origin and destination of containers and sends that information to Beijing, which could even make those machines stop working.
But others are very simple. There is nothing as mundane as a ship dragging its anchor across the seabed for 50 or 100 kilometers, thus breaking the submarine cables through which over 95% of the world's internet traffic travels. However, that is what Denmark, Germany, and Sweden suspect the Chinese bulk carrierYi Peng 3 did in November, intercepted in international waters by the Danish Navy. A month later, Finland seized the tanker Eagle S for a similar incident in its territorial waters, which is part of the ghost fleet that Moscow uses to circumvent international sanctions for the invasion of Ukraine.
The Yi Peng 3 and the Eagle S were allowed to continue their journey after one and two months of detention, respectively, although several crew members of the Russian ship cannot leave Finland. Their cases demonstrate the complexities of combating these types of actions. The Chinese ship had been seized in international waters, limiting Denmark and other countries' ability to detain and inspect it.